Assignment 1
Problem Statement
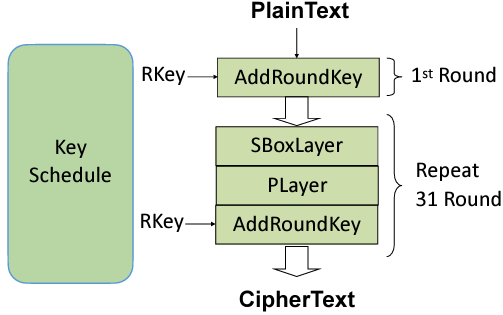
Implement in Verilog the datapath design of the lightweight block cipher, called PRESENT, a symmetric key encryption technique.
Given
The plaintext and ciphertext will be of 64 bits or 8 bytes in size and the encryption key length is 80 bits or 10 bytes.
Below is the high-level block diagram of the PRESENT cipher encryption algorithm.
IMPORTANT: Kindly read the document at this link to create a private repository for the assignment. Do not push everything at the last moment. Maintain a proper commit history.
Part A (Deadline: Jan 25, 2025 11:59 PM)
In this part, you will implement the SBox or Substitution Box design. SBox is a bijection from 4-bits to 4-bits.
The Boolean equation for this design is as follows:
$$y_1 = x_1x_2x_4 \oplus x_1x_3x_4 \oplus x_1 \oplus x_2x_3x_4 \oplus x_2x_3 \oplus x_3 \oplus x_4 \oplus 1$$ $$y_2 = x_1x_2x_4 \oplus x_1x_3x_4 \oplus x_1x_3 \oplus x_1x_4 \oplus x_1 \oplus x_2 \oplus x_3x_4 \oplus 1$$ $$y_3 = x_1x_2x_4 \oplus x_1x_2 \oplus x_1x_3x_4 \oplus x_1x_3 \oplus x_1 \oplus x_2x_3x_4 \oplus x_3$$ $$y_4 = x_1 \oplus x_2x_3 \oplus x_2 \oplus x_4$$
The truth table for this design is as follows:
| $$x$$ | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| $$S[x]$$ | C | 5 | 6 | B | 9 | 0 | A | D | 3 | E | F | 8 | 4 | 7 | 1 | 2 |
You can either use a high level concurrency construct or you can use continuous assignments.
The template code provided to you in file sbox.v is as below.
After completing the design, write the testbench in the provided file tb_sbox.v. Stimulate the input signal of sbox design with all possible input values.
Once completed, ensure the correctness by simulating the design. Use the below commands.
iverilog sbox.v tb_sbox.v -o sbox
vvp sbox
gtkwave sbox_dump.vcd
The expected timing diagram is shown below.
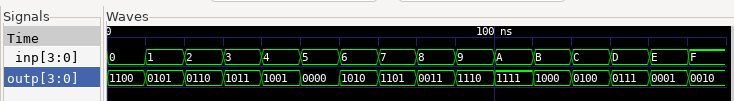
NOTE: The format of values (for ex., binary) on the signals displayed in your GTKwave output may not be similar to the one shown in the output above. Need not worry about it, just make sure that the values are correct as per the specifications of the design.
Part B (Deadline: Feb 01, 2025 11:59 PM)
In this part, you will implement the datapath design of the PRESENT cipher. The datapath will be constructed from keyschedule, permutation and sbox modules as we can see from the block diagram above.
Open the present_cipher.v file and carry on reading further.
The top module present_cipher which implements the design with separate datapath and controller consists of the below interface signals.
The controller design is implemented in the present_cipher.v file. You have to implement the datapath design based on the block diagram shown above.
The signals of interest for the datapath design are round_counter, pstate and kstate. The signals which will be driven by the datapath and necessary for controller are pstate_nxt, kstate_nxt and nxt_rkey.
Three modules are defined in the present_cipher.v file, namely
present_datapath: Datapath design for PRESENT cipherpresent_keyschedule: Key Schedule designperm: PLayer or bit-permutation design
Have a look at the provided comments in the respective modules and implement the respective designs.
Copy the sbox.v file from the part-a to part-b directory, so that the datapath design can use it.
NOTE: DO NOT make any changes to the top module named
present_cipher.
IMPORTANT: We recommend you to write individual testbench for checking the correctness of your
present_keyscheduleandpermmodules. Its a good practice to verify each module before using them with other modules.
This is an optional step but we highly recommend it.
For ensuring the correctness of your datapath design, we have provided the testbench file tb_present_cipher.v. DO NOT make any changes to this testbench.
Use the below commands to simulate your design.
iverilog present_cipher.v sbox.v tb_present_cipher.v -o present
vvp present
gtkwave present_dump.vcd
You shall see the below timing diagram in GTKwave.
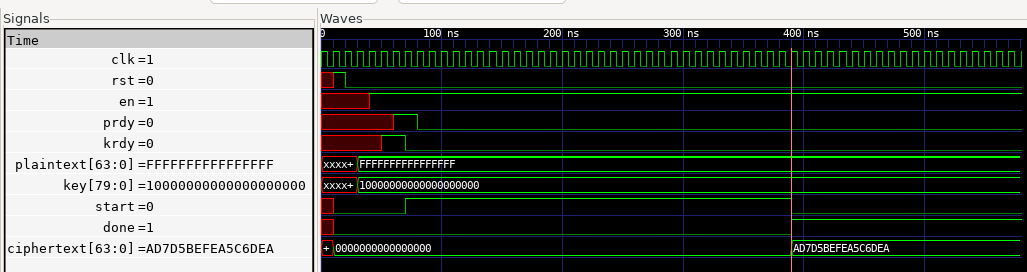
NOTE: In the provided testbench, the
plaintext = 64'hffffffffffffffffandkey = 80'h10000000000000000000. Hence the corresponding output forciphertext = 64'had7d5befea5c6dea.
NOTE: The format of values (for ex., hexadecimal) on the signals displayed in your GTKwave output may not be similar to the one shown in the output above. You can change it to hexadecimal by doing a right-click on a signal and update its radix to
Hexadecimal.
We are providing a C implementation of the PRESENT cipher design in present_cipher.c file. Compile the file and provide the plaintext and key input in the hexadecimal format to see the corresponding ciphertext output.
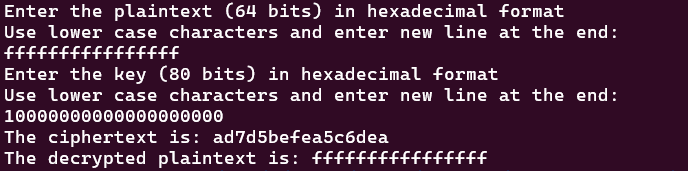
You can then use the respective combination of plaintext and key in the testbench to ensure whether your datapath design is able to produce correct ciphertext.
Submission
Part A
Rename the part-a directory to <team-name>_a1_parta. The directory MUST contain these files:
sbox.vtb_sbox.v
Compress this directory into a tar.gz file using the command:
tar -czvf <team-name>_a1_parta.tar.gz <team-name>_a1_parta
Upload this <team-name>_a1_parta.tar.gz on the Moodle at the respective link for Part A.
Part B
Rename the part-b directory to <team-name>_a1_partb. The directory MUST contain these files:
present_cipher.vsbox.v
Compress this directory into a tar.gz file using the command:
tar -czvf <team-name>_a1_partb.tar.gz <team-name>_a1_partb
Upload this <team-name>_a1_partb.tar.gz on the Moodle at the respective link for Part B.
IMPORTANT: Apart from updating your team's private GitHub repository for this assignment, you also need to upload your submission on Moodle.